Menu
STOP IT
WITH THE
SIEM RULES.
WITH THE
SIEM RULES.
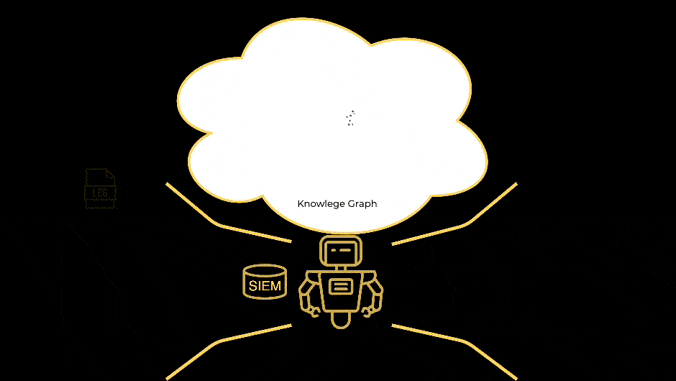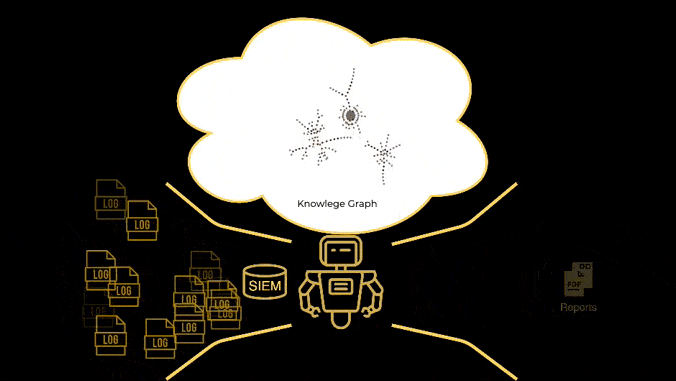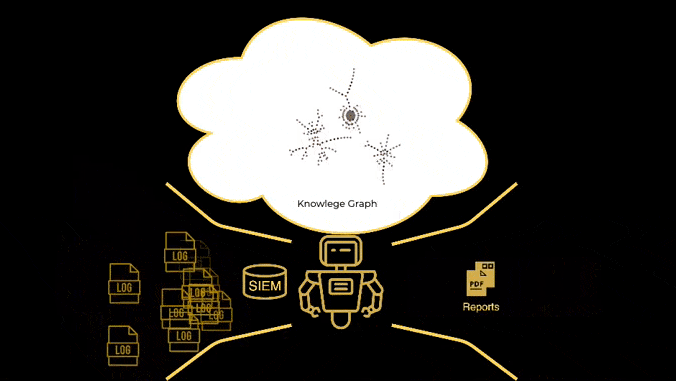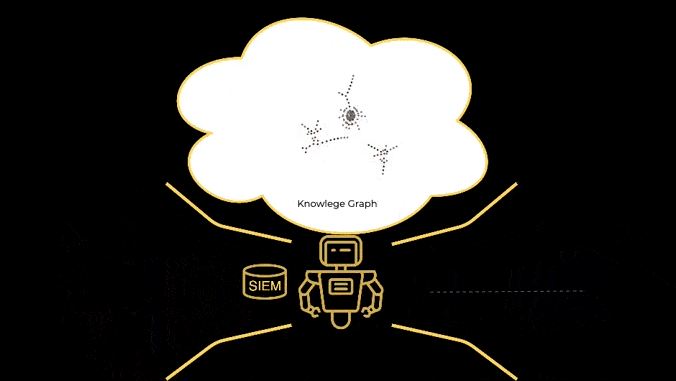
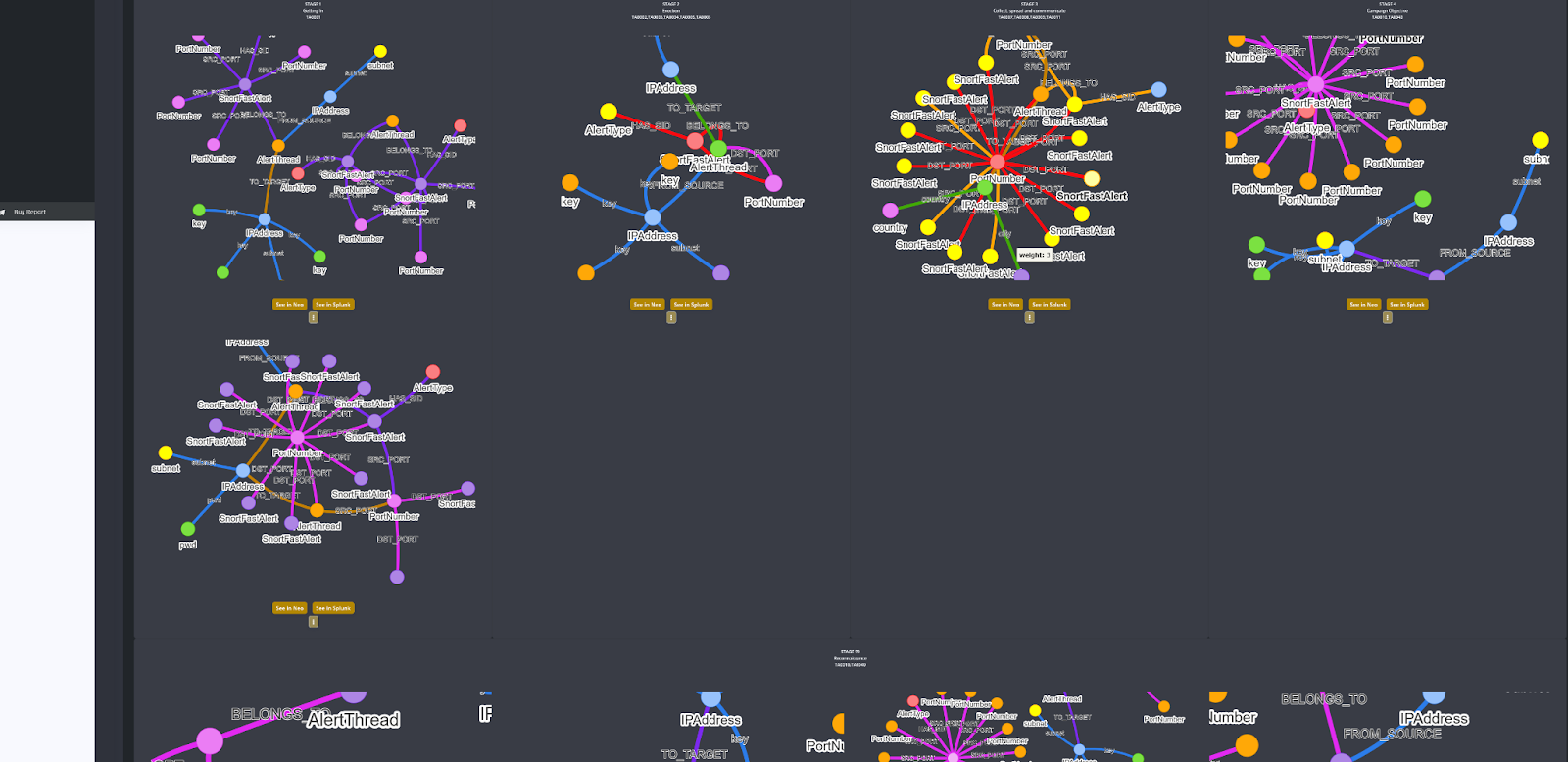
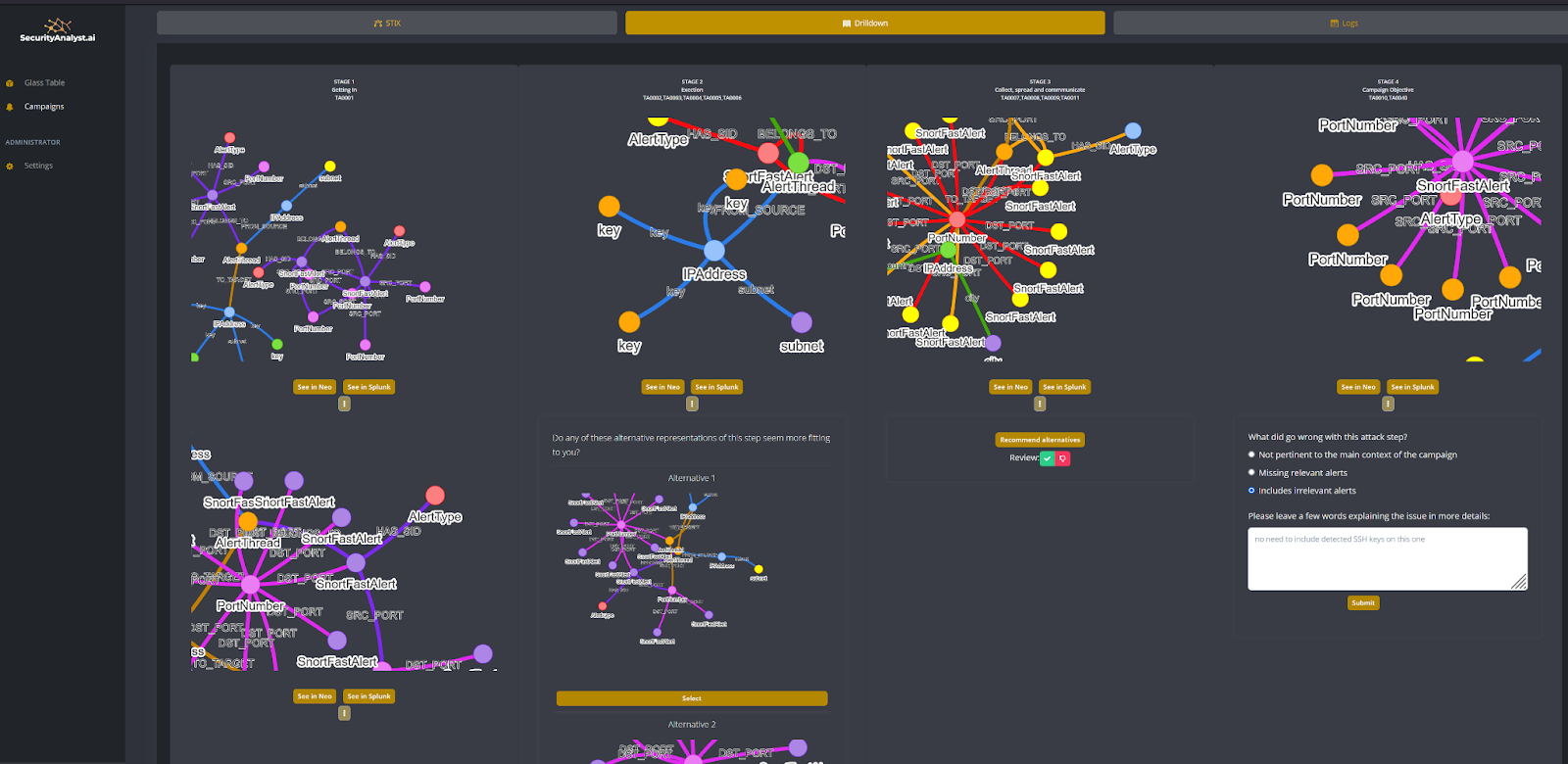
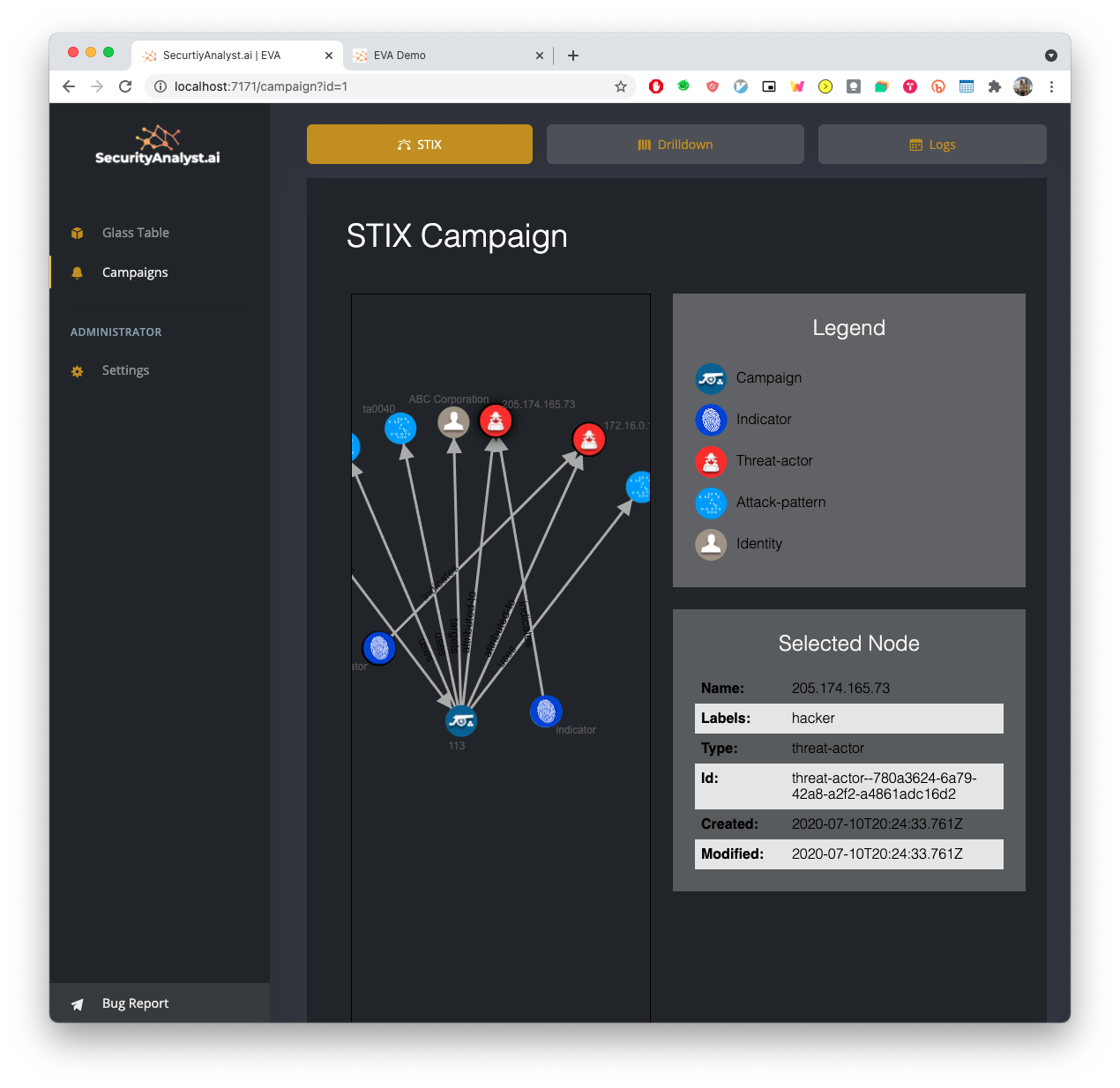
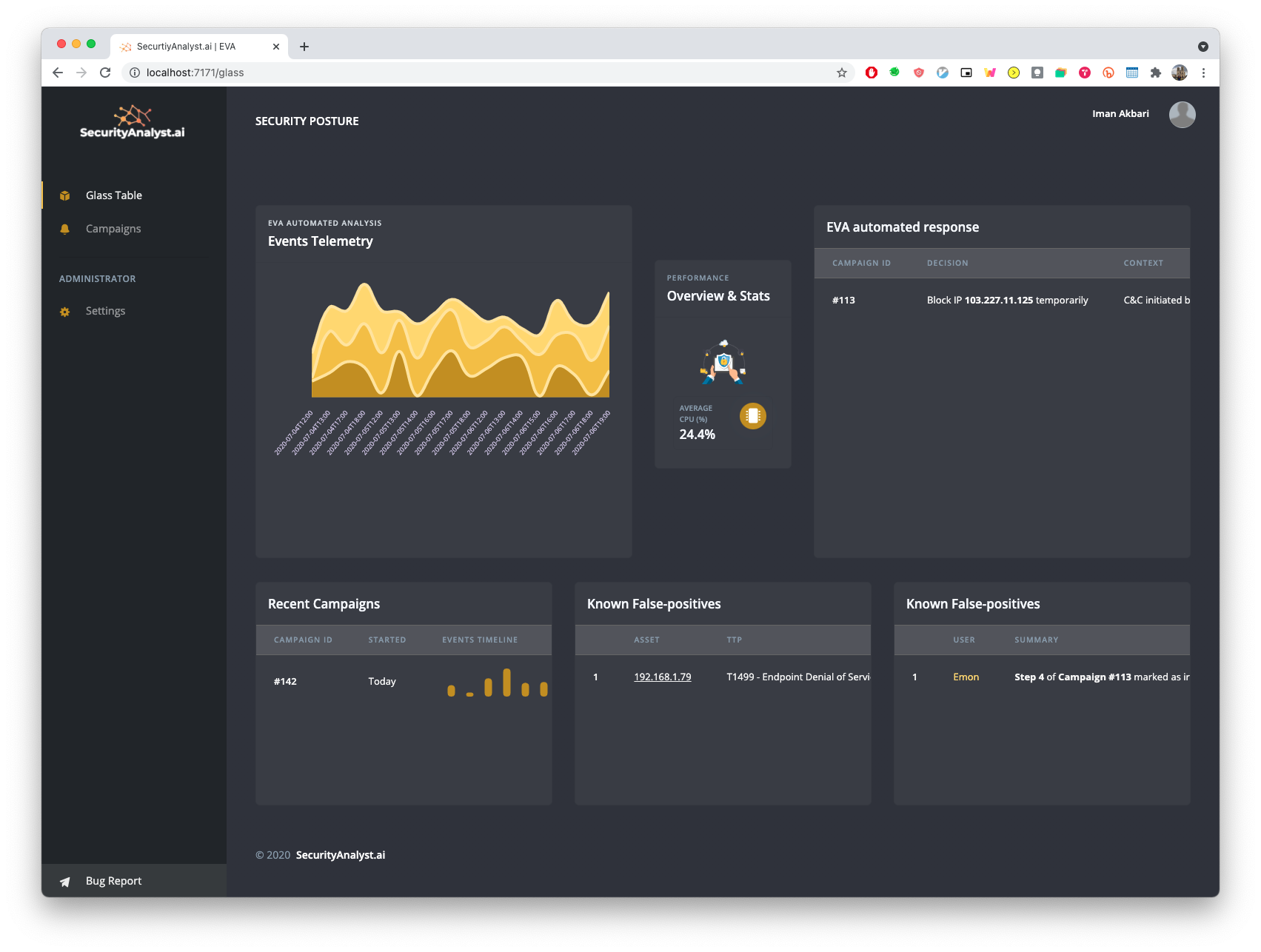
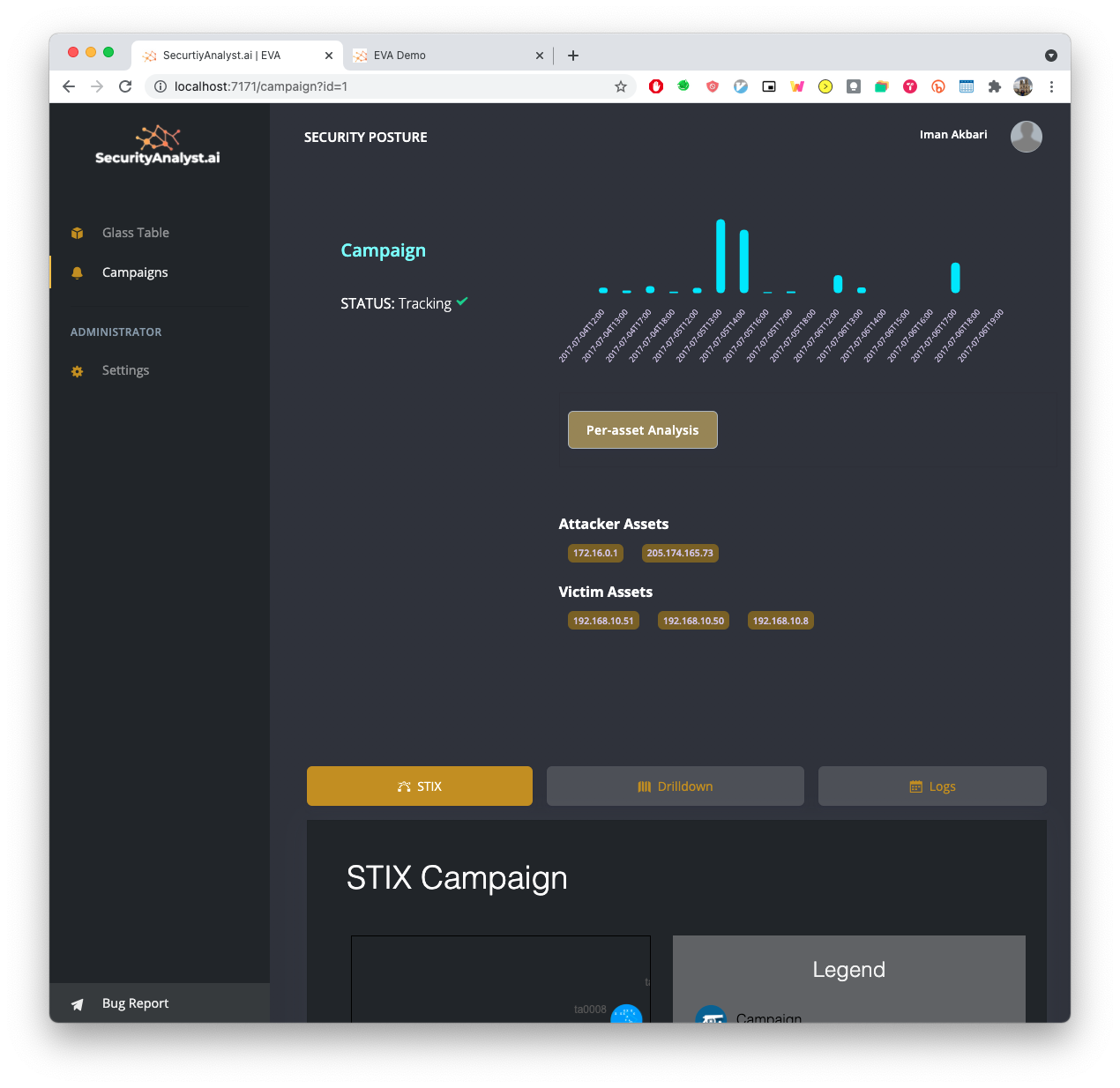
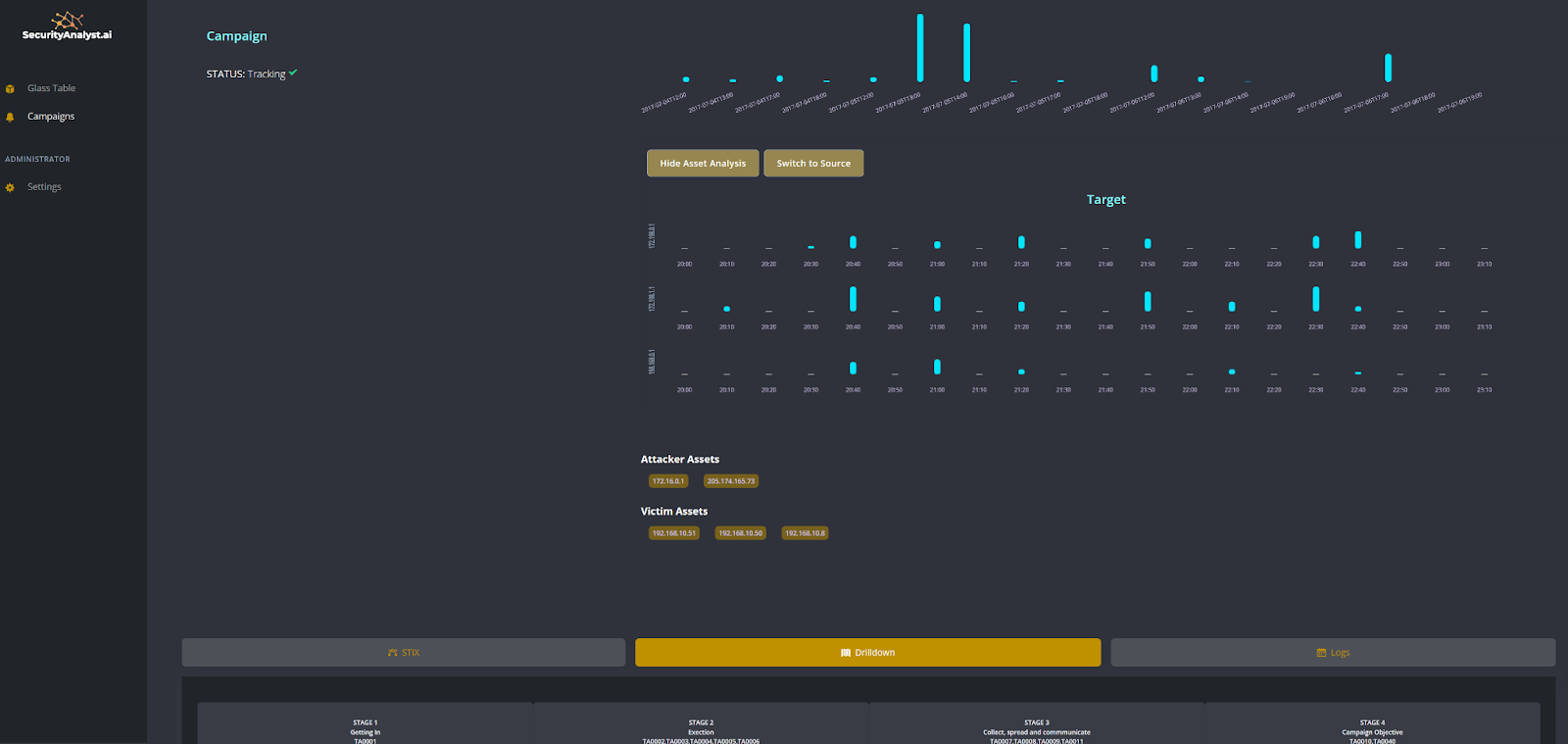
No rules, no playbooks, no notebooks, no threat hunts, no training period, no secret sauce, no nonsense. Simple AI based monitoring, detection and response, based on knowledge graphs, and MITRE ATT&CK.
Built by SOC analysts for SOC analysts.
Play Video